
Thank you to Neil, Sudhakar and Brady for the feedback and review.
Decentralized Physical Infrastructure Networks (DePIN) are fundamentally changing how real-world resources—like bandwidth, sensor data, computation, and wireless connectivity, are provided, measured, and monetized.
As the sector matures, DePIN projects face an increasingly strategic question: Should proofs of network activity or resource contribution be stored directly on-chain, or is off-chain validation sufficient?
This is not just a technical dilemma.
As DePIN grows from a $30-50 billion industry today to a projected $3.5 trillion market by 2028, the way each project chooses to store and validate proofs will shape trust, access to enterprise markets, regulatory compliance, and even the potential for premium pricing.
For some projects, especially those aggregating and selling verifiable data, storing proofs on-chain is quickly becoming the norm.
The need for public, tamper-proof audit trails is being driven by enterprise clients, regulatory requirements, and the need to demonstrate uncompromising transparency.
For others, particularly those focused on delivering real-time compute or bandwidth, on-chain proofs are often seen as unnecessary operational overhead. In these cases, off-chain validation strategies are still the industry standard.
The question of on-chain versus off-chain proof storage is ultimately about trust, how it is established, maintained, and transferred between different stakeholders.
In data-centric DePINs, trust must be projected outward to enterprise customers, auditors, or regulators who did not directly witness the activity that generated value. These stakeholders rely on immutable, independently verifiable records to confirm that claims are legitimate and untampered. On-chain proofs provide exactly this: a transparent, lasting audit trail that anyone can check, now or years into the future.
In contrast, service-focused DePINs provide live access to resources such as computation or bandwidth, where users themselves experience and verify the outcome in real time.
In these contexts, customers do not typically require ongoing, public proofs because they are able to immediately observe whether the service is working as promised.
Unless specific regulatory or anti-fraud requirements are imposed from the outside, the need for on-chain auditability is much less pronounced. Thus, the choice of proof storage is deeply tied to the project’s product, business model, and who needs to trust the data.
It’s also important to note that these models serve different users.
Data aggregation DePINs are mostly B2B, selling to enterprises or institutions that need lasting, auditable records. Service-based DePINs, on the other hand, mainly serve retail users who interact with the service directly and judge its quality in real time.
This difference explains why enterprises demand robust on-chain proofs, while retail users are satisfied with instant feedback.
Below we compare two distinct types of Decentralized Physical Infrastructure Networks, and how their subtle differences impact their on-chain proof storage needs.
Data aggregation DePINs focus on delivering datasets—such as environmental, sensor, or web-scraped data—to external buyers like enterprises, AI labs, and regulators.
Since these customers don’t directly witness data creation, they need a reliable way to confirm its authenticity and integrity. For these networks, on-chain proof storage isn’t just a technical feature—it’s essential for enabling auditability and trust.
Take Grass Protocol as an example.
By anchoring cryptographic proofs of each dataset on-chain, Grass allows buyers to independently verify the data’s source and integrity. This approach has helped Grass win enterprise clients, justify premium pricing, and stand out in the market.
Environmental monitoring networks show the same pattern.
Customers, such as sustainability auditors and government agencies, need immutable records to validate claims like carbon credits or pollution levels. Storing proofs on-chain creates a tamper-proof audit trail, making these claims robust in both regulatory and legal contexts.
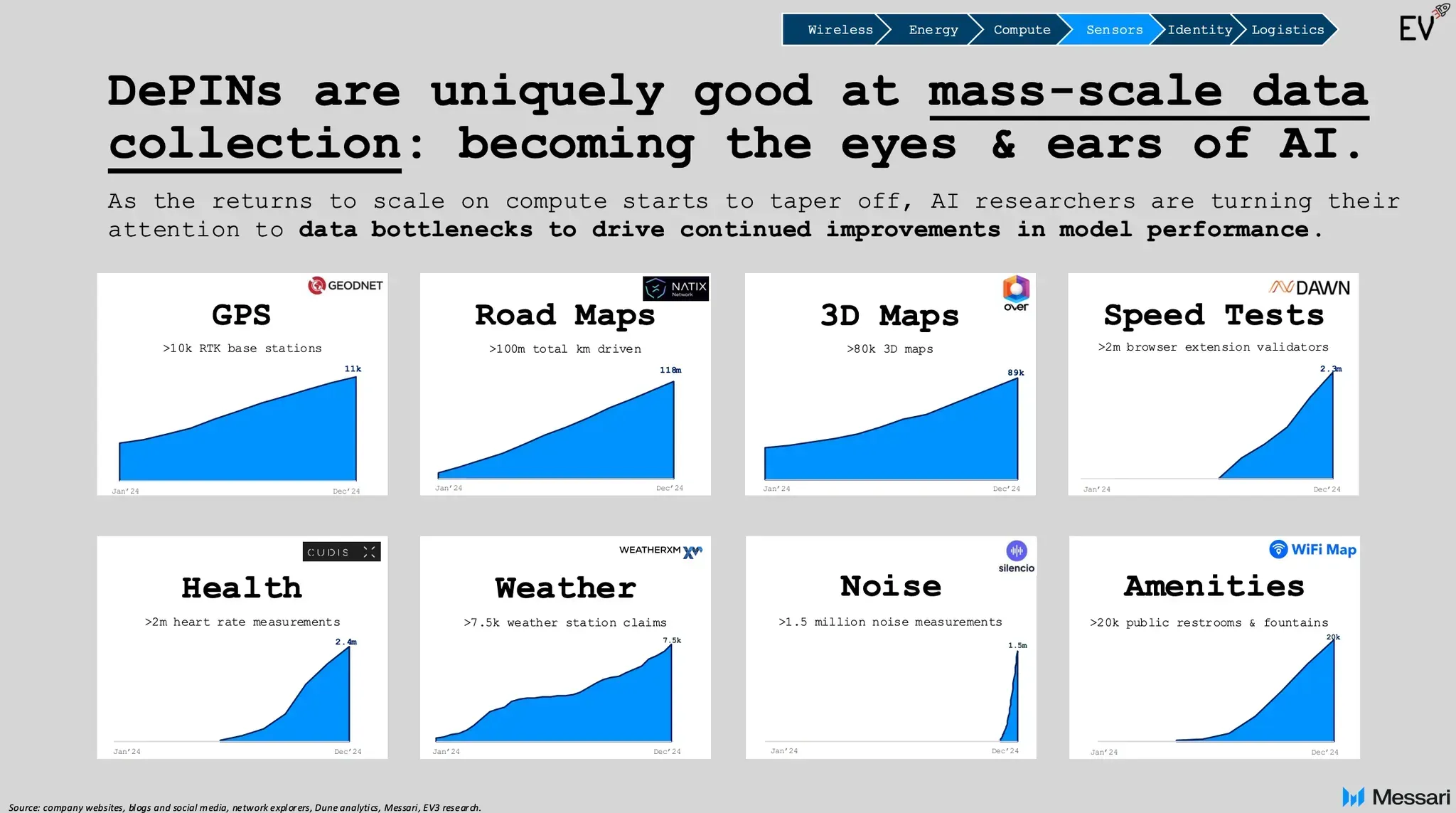
Service-based DePINs provide resources like compute power, storage, or bandwidth that users can verify directly as they use them. If the service fails, customers notice right away—so there’s less need for ongoing, public proofs.
For example, io.net aggregates decentralized GPU and CPU resources. Instead of storing every usage proof on-chain, io.net validates most activity off-chain and only settles payments on Solana. This keeps costs low and allows for high transaction volumes, showing that customers in this space care more about efficiency than exhaustive, on-chain records.
Other networks, such as decentralized CDNs and wireless protocols, take a similar approach. They use internal or peer-to-peer checks to ensure quality and prevent fraud, but only rely on on-chain records for payments, slashing, or dispute resolution. As a result, they can operate efficiently at scale without needing to log every action publicly.
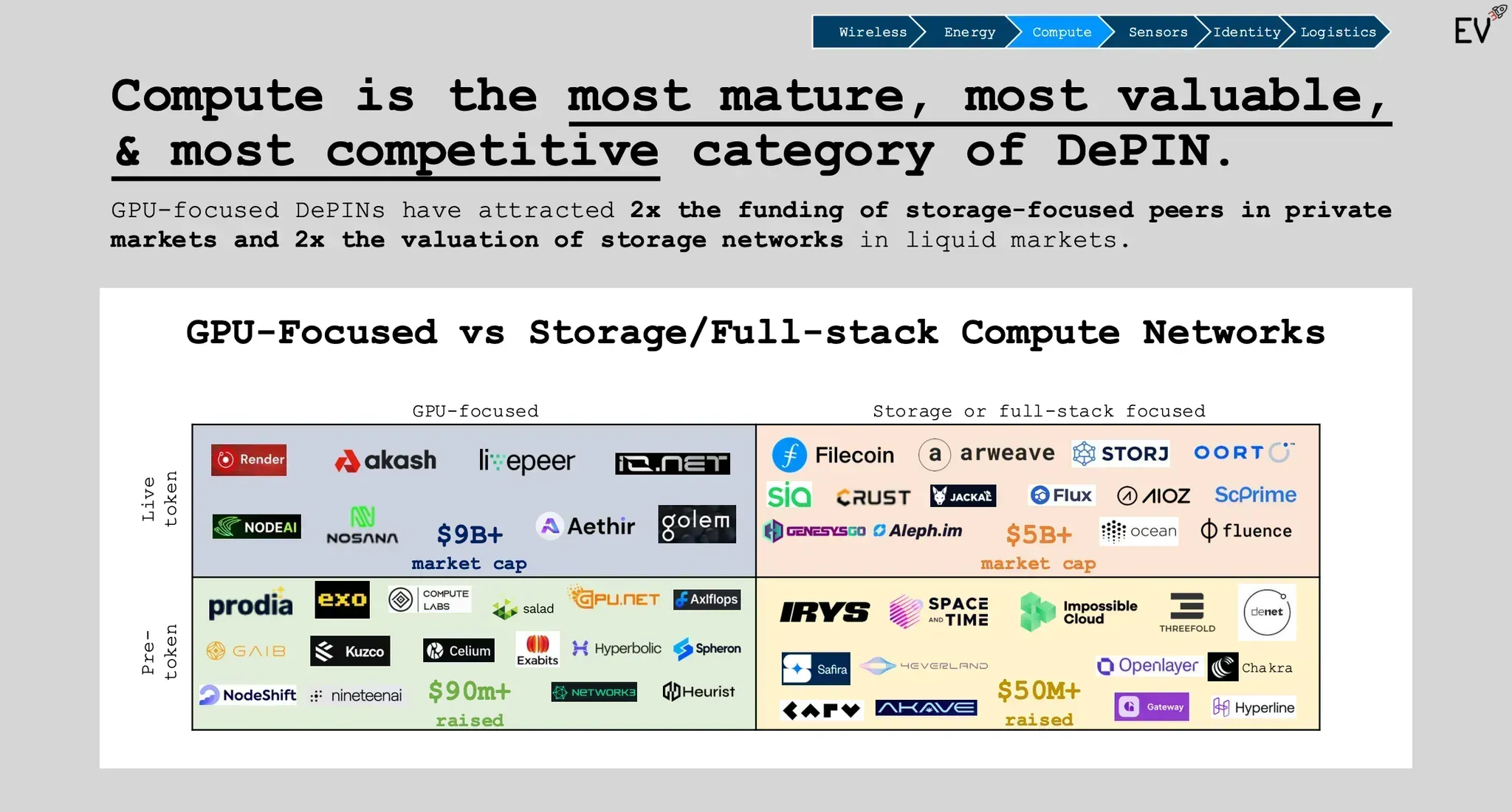
The main difference between proof storage strategies comes down to how trust is established.
For data aggregation DePINs, data gets separated from its source, so buyers need lasting, verifiable proof that it’s authentic. On-chain cryptographic proofs are the only scalable way to guarantee this, creating a transparent audit trail that anyone can verify.
For service-based DePINs, trust is based on direct user experience. Users interact with the service in real time and can immediately tell if it works as promised. Because of this, ongoing public proofs aren’t usually needed unless outside parties like regulators demand extra assurances.

Let's look at three examples of using this framework in practice.
Grass Protocol is an example of a network that has made on-chain proofs central to its business. By providing cryptographic, on-chain proofs for every dataset it delivers, Grass gives AI labs and data buyers a way to verify provenance and timestamp independently.
This level of transparency has allowed Grass to attract enterprise clients and justify premium pricing, supporting seven-figure monthly revenues. For these customers, auditability is not just a technical feature—it’s the foundation for trust and commercial relationships.
On the other side, io.net aggregates compute resources and validates most actions off-chain. Payments and settlements are processed on Solana, but most operational data and proofs never touch the blockchain. Instead, these proofs are used internally to calculate node rewards. This has enabled io.net to scale efficiently, keeping costs down while still delivering a reliable, high-performance service.
Their success demonstrates that off-chain validation remains sufficient, when real-time experience is the primary basis of trust.
Sensor and environmental networks frequently face requirements for compliance, legal defensibility, and third-party audit. Here, storing proofs on-chain is crucial, as it creates a tamper-evident public record that can withstand scrutiny by regulators and legal adversaries. These networks show how regulation can push entire DePIN verticals toward adopting on-chain storage as a baseline, not just an enhancement.
DePIN projects today typically choose among three main approaches for proof storage, each offering different tradeoffs in terms of transparency, auditability, access control, and operational complexity.
Below we summarize these methods and highlights real-world examples of how they are used across the Solana DePIN ecosystem.
All proof data (or its hash/metadata) is written directly to Solana accounts, PDAs, or as on-chain metadata. On-chain proof storage is publicly accessible and fully verifiable making it highly auditable. The tradeoff for being the most transparent and tamper-proof storage option is a higher cost and storage limits.
Some notable examples include:
DePIN proofs are stored on third-party or decentralized storage networks like S3, IPFS, and Arweave. The integrity of the proofs can be checked if the hashes are public, and they can be accessed by anyone, however sometimes access requires a fee. While storing ZK proofs off-chain is cheaper than storing them on-chain, the tradeoff is users must trust data availability and the proofs must be linked correctly.
Some notable examples include:
Proofs are kept on internal servers or permissioned systems. The auditability and accessibility of off-chain private DePIN proof storage is low because it is limited to insiders, operators, and partners. While private, off-chain proof storage is the most affordable option for internal operations, it is not transparent to the ecosystem or end users.
Some notable examples include:
In practice, teams choose among these three proof storage methods based on what their users, partners, or regulators require.
Projects like Grass anchor proofs on-chain to maximize transparency and trust for external customers and auditors.
Networks like Helium opt for off-chain public storage to keep costs low while still allowing some form of external access.
Compute marketplaces such as io.net often keep proofs private, prioritizing speed and operational simplicity over external auditability.
The choice of method depends on the network’s trust model, target customer base, and compliance environment.
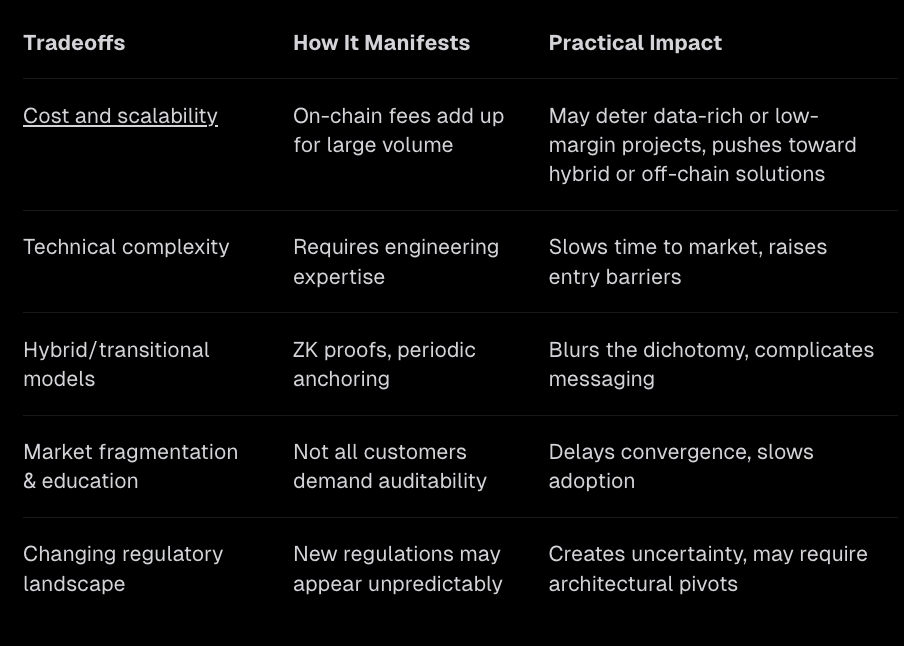
On-chain proof storage isn’t free of tradeoffs. Recording lots of proofs on-chain can be costly, especially for networks with high transaction volumes or tight margins. Running and securing on-chain systems also requires specialized skills, which can be a hurdle for smaller teams. Hybrid solutions—like periodic anchoring or zero-knowledge proofs—can reduce these costs but add technical complexity.
Customer demand is also uneven. Retail users typically don’t care about auditability and are comfortable trusting the service, which slows the push for on-chain adoption. In contrast, enterprises and institutions do care, they expect some form of verifiable proof, whether on-chain or at least robust off-chain records.
Finally, because regulations can change unexpectedly, teams need to stay flexible and plan for shifting requirements.
The question of on-chain versus off-chain proof storage will become a debate in the evolution of decentralized infrastructure. This research shows that the right answer depends on a project’s business model, customer needs, and the broader sector it operates in.
For data aggregation DePINs—especially those targeting enterprise, research, or compliance-driven markets—on-chain proof storage is quickly becoming a baseline requirement.
Here, the ability to provide verifiable provenance, achieve regulatory compliance, and command premium pricing all depend on maintaining an immutable, auditable record.
For service-based DePINs focused on real-time delivery of resources, off-chain validation and hybrid approaches are typically enough, provided that users can directly observe and verify service quality.
In practical terms:
We project that as technical and economic barriers to on-chain proof storage continue to fall, especially with the rise of new tooling, more DePIN networks—particularly those in data-heavy or compliance-driven sectors—are likely to adopt on-chain proofs as a default.
Projects that align their proof strategy with their product and user requirements will be best positioned to earn trust, reach high-value markets, and sustain adoption as DePIN matures.
This research article was prepared by Nitro Labs, developer of Termina’s Data Anchor, a proof-anchoring solution for Solana.